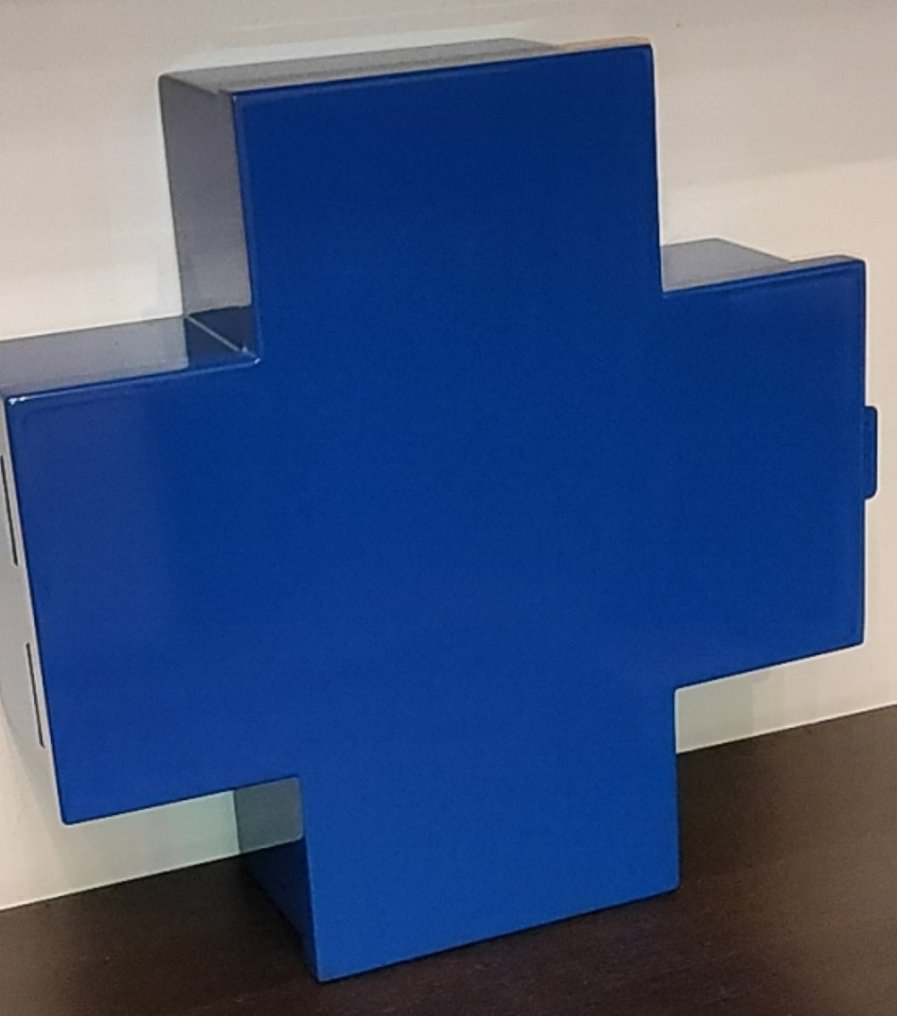
Thomas Eriksson Cross Cabinet in Green Glossy Metal for Cappellini For Sale at 1stDibs | cappellini cross cabinet

Bathroom/medicine cabinet, 'Cross', designed by Thomas Eriksson 1992 for the collection Progetto Ogetto by Cappellini. - Bukowskis

Black and white bathroom with Capellini medicine cabinet and Jatana tiles. Brooke Aitken Design | White wooden box, White bathroom, Lighted bathroom mirror
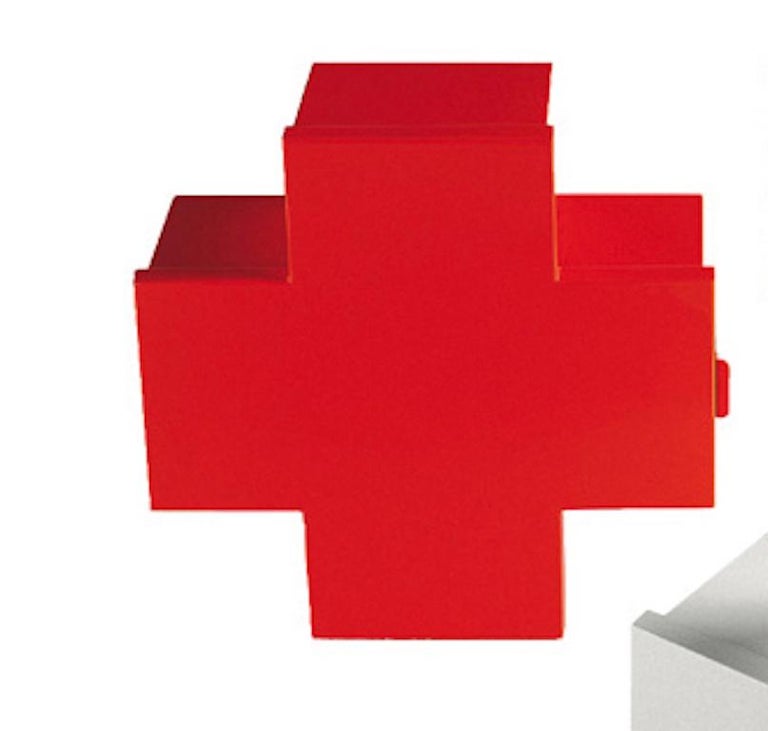
Customizable Thomas Eriksson Cross Cabinet with Glossy Varnished Finish for Cappellini For Sale at 1stDibs | cappellini cross cabinet, cross cabinets

394: THOMAS ERICKSSON, Cross medicine cabinet < Taxonomy of Design: Selections from Thessaloniki Design Museum, 25 August 2016 < Auctions | Wright: Auctions of Art and Design

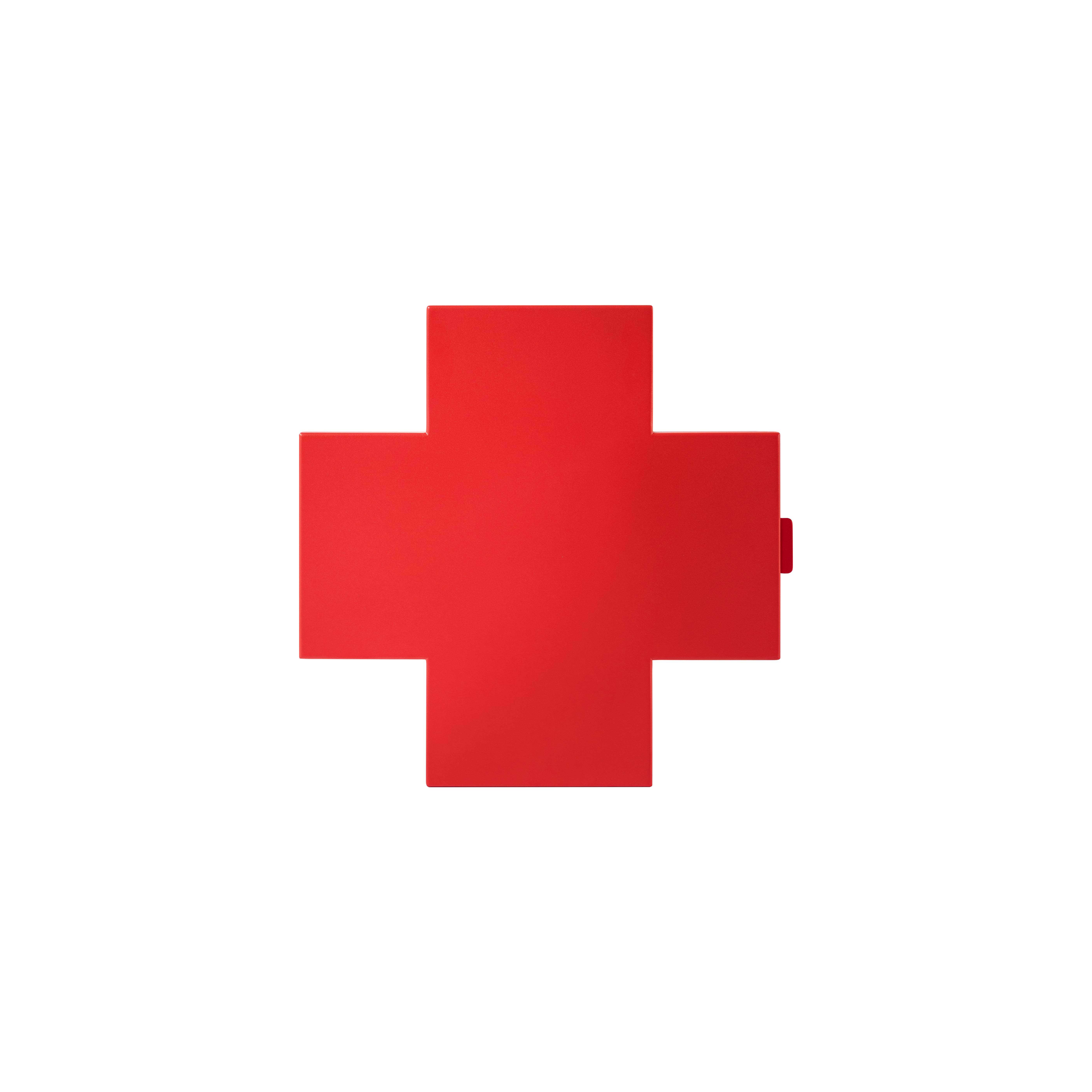
Thomas Eriksson Cross Cabinet in Red Glossy Metal for Cappellini For Sale at 1stDibs | cappellini cross medicine cabinet, red cross medicine cabinet